Our customer survey has been sent out 8658 times as of the 26/09/2017 and below are the results:
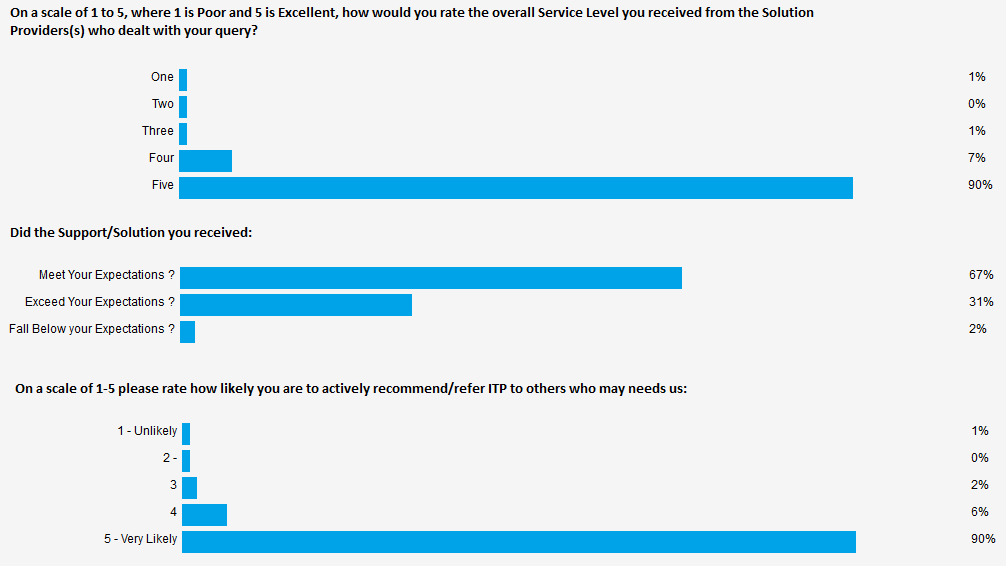
Our customer survey has been sent out 8658 times as of the 26/09/2017 and below are the results:

One of our Partners sent us over the information below:
On August 9, the first campaign of a massive, worldwide ransomware attack was detected—and 62,000 phishing emails related to the attack have been identified as of last week. This new Locky-variant continues to unfold, powered from more than 11,625 distinct IP addresses in 133 different countries (the top five being Vietnam, India, Mexico, Turkey and Indonesia). As an MSP, here’s what you need to know about this new Locky-variant ransomware and how you can ensure you remain protected against it.
Locky is a common type of ransomware that emerged in 2016 and has since been utilized in a wide range of cyber attacks. However, this new variant is one we have not seen before. So, how exactly does this variant work?
The main way this Locky-variant is spread is by social engineering. Through phishing emails, users are tricked or induced into opening a docx, pdf, jpg, zip or other file containing the ransomware called “IKARUSdilapidated,” after a phrase that appears in the code string. If the user follows through and opens the attached file, the ransomware then takes over.
From here, all files that match particular extensions are encrypted and filenames are converted to a unique 16 letter and number combination with the .locky file extension. After the files are completely encrypted, users are given instructions for downloading a Tor browser and directed to a site on the dark web where the cyber criminals demand a ransom payment of up to one bitcoin (which equates to over $4,000).
Many endpoint protection solutions have been updated to detect Locky ransomware, however, this variant is able to slip past certain tools because it is so new. Thus, as a new ransomware variant, it is read as an “unknown file” and is allowed entry by organizations not using a “default-deny” security posture (which denies entry to all unknown files until it is verified that they are safe to enter the IT infrastructure), making it more difficult to detect and remediate.
Due to this it is vital that you never open an email attachment unless you are positive you know where and from whom it has come from.
Unfortunately, no matter how strong your security solutions, attacks will continue to slip through the cracks. Therefore it’s very important that you have a proper, reliable backup and disaster recovery solution with online and offline backup solutions as the ultimate failsafe against successful attacks.
Please feel free to contact us regarding this and we’ll be more than happy to help.